30+ threat model data flow diagram
This information is documented in a resulting Threat Model document. Operational or infrastructure threat models OTMs are a specific type of data flow diagram visualising how the independent grouped and shared components communicate.
A Comprehensive Guide To Flowchart With 50 Examples Cybermediana
Microsofts Threat Modelling Tool This tool identifies threats based on STRIDE threat model classification and.
. Module 8 Units Beginner Administrator Developer DevOps Engineer. Threat Model Thursday. You can ignore the message or you can follow the instructions to fix the issue.
The analysis uses a Data Flow Diagram DFD to describe how data. The DFDs show the different paths through the. In this step Data Flow Diagram should be divided in the context of Model View Controller MVC.
A Data Flow Diagram DFD as the name indicates shows the flow of data through the system. Data flow diagrams are very frequently used in threat modeling. Microsoft 365 Security Center Cloud App Security Data-flow.
Once added their ends can be dragged around the. This white paper looks at some flaws and the advantages of moving to a more mature Process Flow Diagram PFD approach to threat modeling as a solution. If you create a threat model and forget to connect data flows to elements you get a notification.
A Data Flow Diagram DFD for Minesweeper a game that ships with WindowsTM is shown in Figure 1. Visual Paradigm Online features an online threat model maker and a large variety of technical and. This weeks threat model Thursday looks at an academic paper Security Threat Modeling.
Threat modeling analyzes how an adversary might attack a system by supplying it with malicious data or interacting with it. Some of the most valuable key. Create a threat model using data-flow diagram elements.
It is also used to produce data flow diagrams DFDs for the application. We represent a DFD as a runtime view following the Component-and-Connector. Create threat models online.
It depicts external entities processes data stores and data flows. Use a data flow threat model analysis with the aid of intelligence tools to determine additional areas that are outside the boundary of common knowledge. In this longest episode of the worlds shortest threat modeling videos I introduce the five.
Are Data Flow Diagrams Enough. Data flows and trust boundaries can be added to the diagram by clicking their shape in the stencil on the left side of the diagram editor. Currently eight tools are available for Threat Modelling.
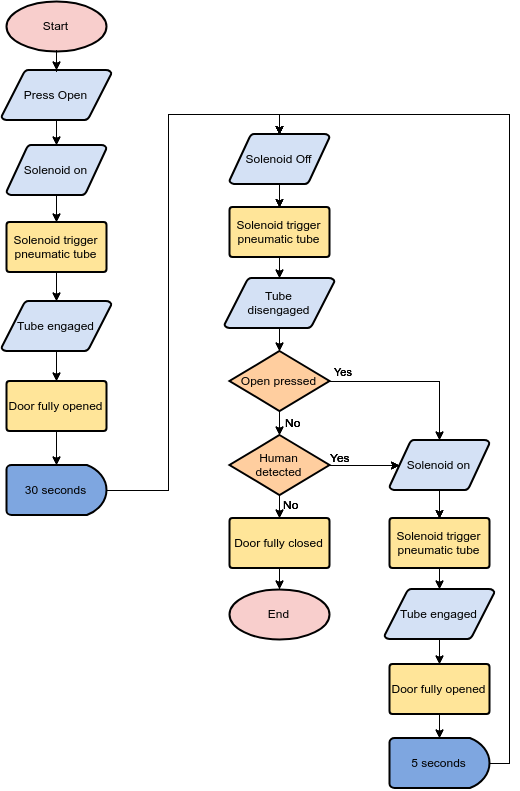
Use tools to draw your diagram If you dont like to manually draw your DFD. A threat model diagram is a visual form of threat model.
T2isd79la4he3m

Graphing The Utility Grid On Aws Aws For Industries
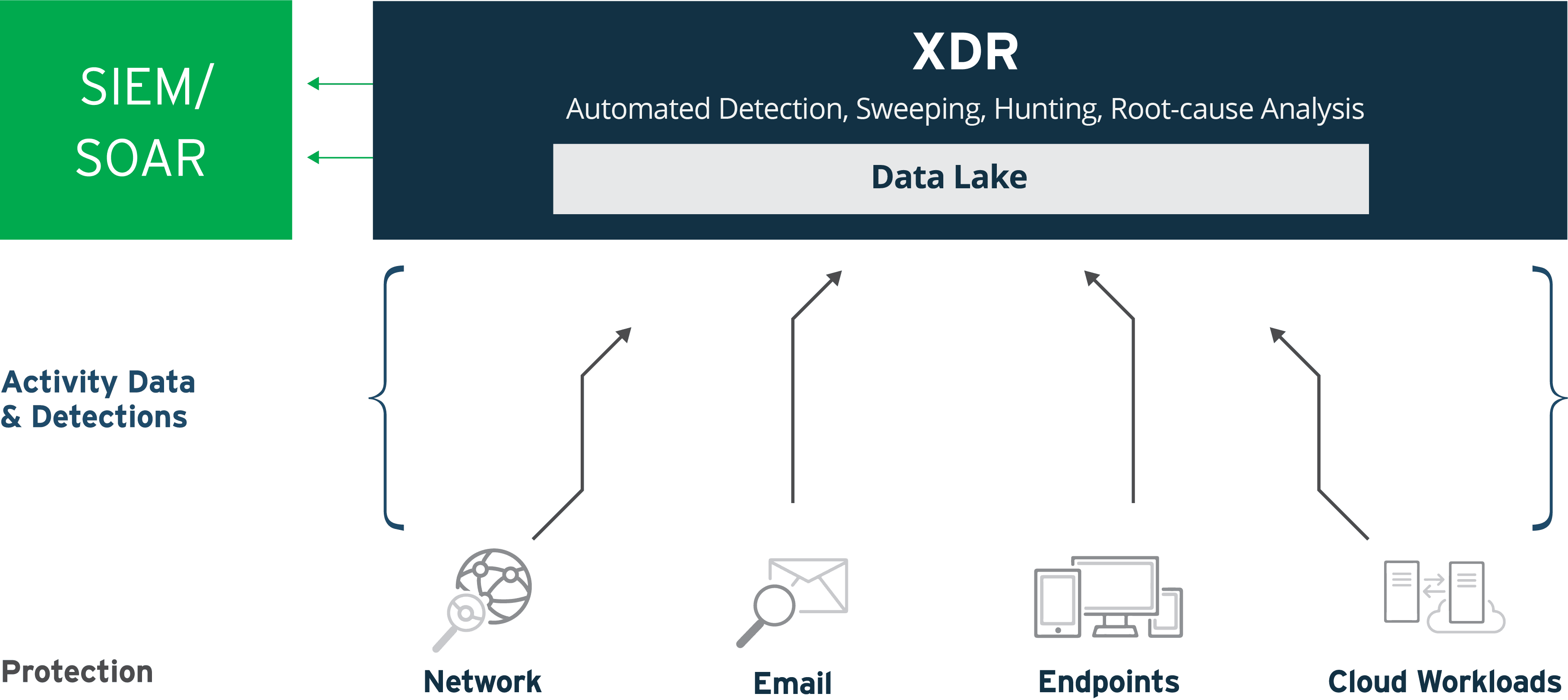
What Is Xdr

Actionable Insights For Improved Business Results Atscale
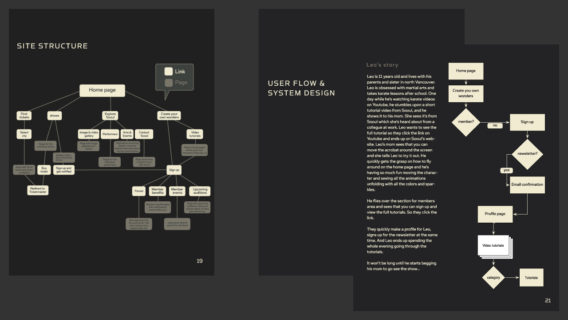
How To Design A User Flow Diagram For Your Website
How To Design A User Flow Diagram For Your Website
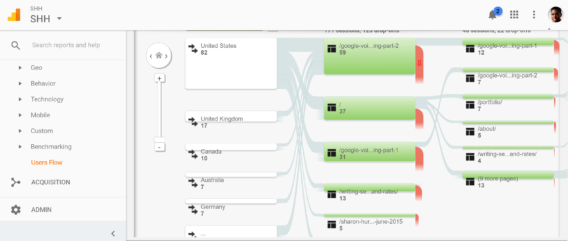
What Is The Purpose Of Developing Dfds Quora
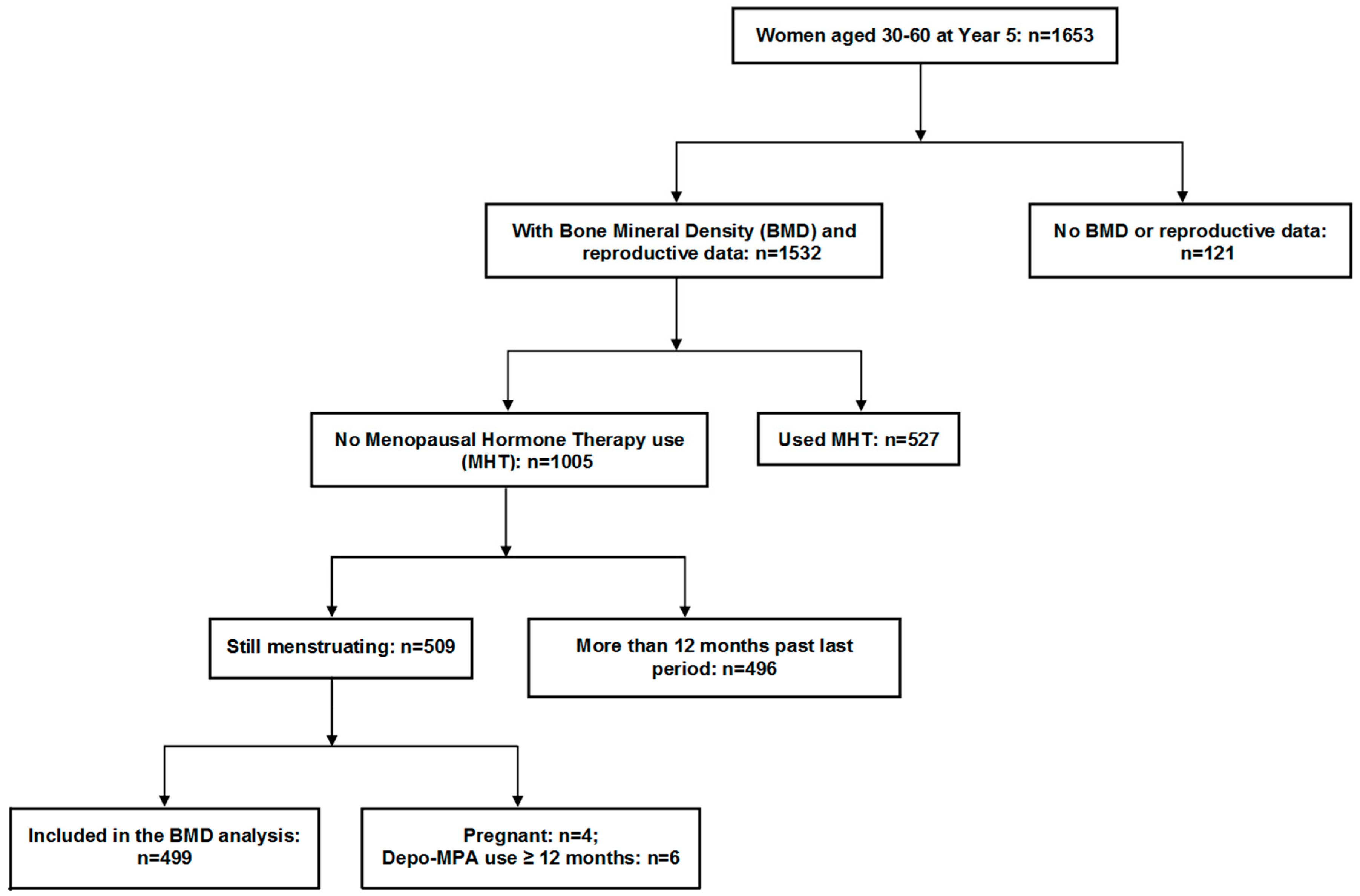
Ijerph Free Full Text Adult Premenopausal Bone Health Related To Reproductive Characteristics Population Based Data From The Canadian Multicentre Osteoporosis Study Camos Html

Code Quality Tools Tame Software Complexities Circuit Cellar
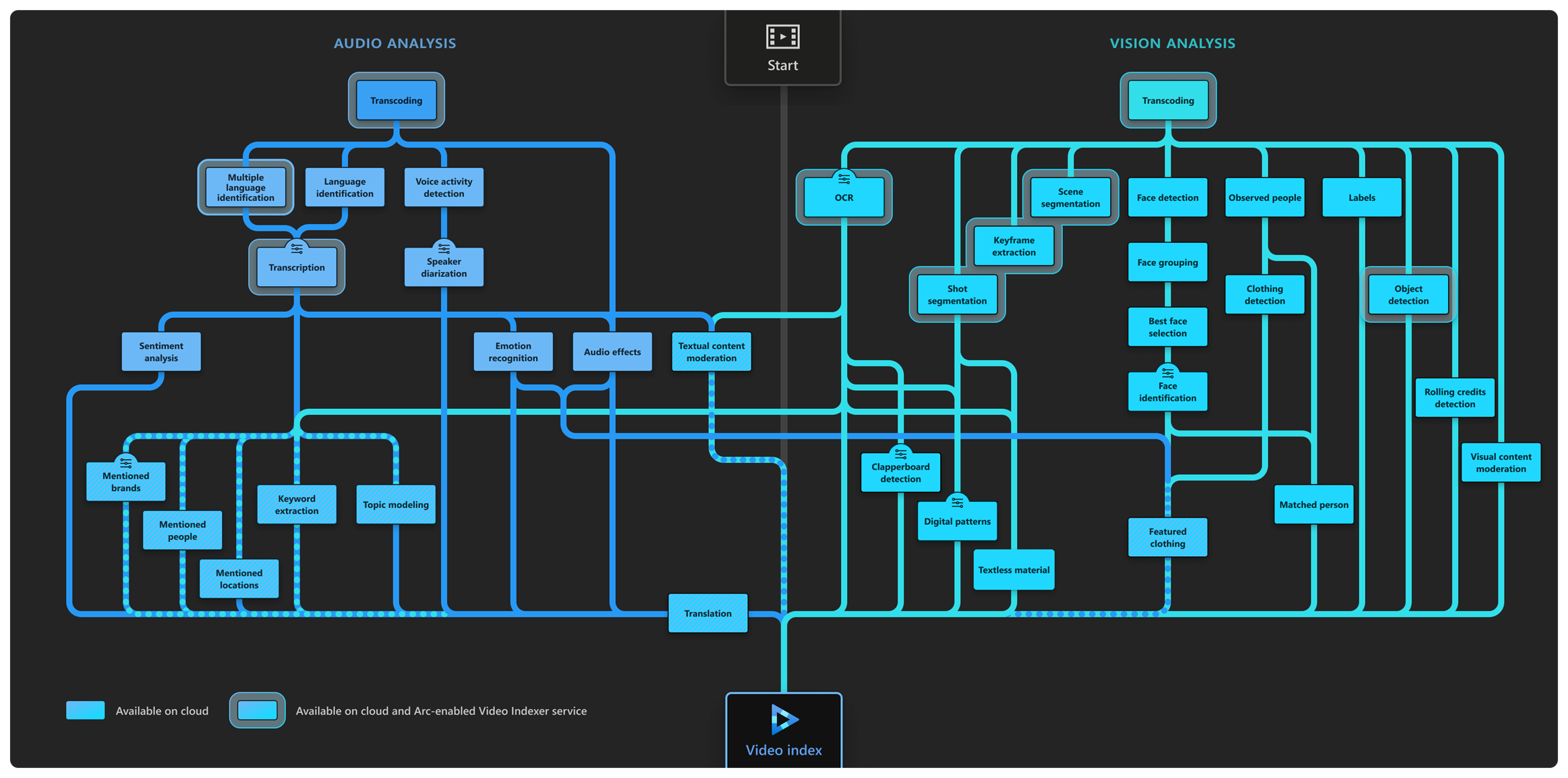
What Is Azure Video Indexer Azure Video Indexer Microsoft Learn

Graphing The Utility Grid On Aws Aws For Industries

A Threshold Based Real Time Analysis In Early Detection Of Endpoint Anomalies Using Siem Expertise Sciencedirect

Real Time Operational Monitoring Of Renewable Energy Assets With Aws Iot Aws For Industries
Top 35 Business Analyst Interview Questions And Answers 2022

Navin Ramankutty Nramankutty Twitter
![]()
Threatmodeler About The Evolution Of Threat Modeling
100 Ai Use Cases Applications In 2022 In Depth Guide